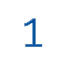INTEGRATION PROCESS
Integration Process methodology for future use by the client when the time comes to select the integration vendor. The diagram below details each step in the process and is followed by a short description of each step
- Meeting to learn requirements, goals, and objectives
- Discuss approaches, architectures, benefits, and trade-offs
- Evaluate cyber-security and social engineering policies
DISCOVER We approach each integration project openly to first gather the information needed to ensure that all parties involved understand the overall objectives and complexities of the project.
- Build staff knowledge on CIM and approach to model-driven integration
- Focus on technical and process issues
TRAIN Training on the underlying CIM technology and the processes to utilize those standards helps build staff knowledge and the skills needed for all team members to understand the integration approach and work together effectively.
- Requirements
- Use Cases
DOCUMENT Formally documenting the requirements and business use cases is a critical step by providing formalized information that ensures subsequent activities are undertaken in a way that serves the ultimate goals and objectives for the project. Interfaces to the external integration points are identified and documented.
-
Develop data exchange model including model extensions as well as model and message profiles using the CIM
MODEL Based on the use cases, the standard CIM model is used as the starting point to develop the data exchange model used for the integration architecture. Extensions needed to fulfill the use cases are defined. A model profile is generated that removes the unused elements from the standardized model enabling adapter design. If needed, message profiles are created to define the message schemas, which describe the payloads. As an alternative, model profiles may also be generated as part of this step to provide a model exchange capability.
- Message payloads and Model Profiles and test plans including interoperability
- Application Adapter design
DESIGN During development, the use cases and the IEC specifications (either 61968-4 through 9 or 61970 model exchange standards) guide the definition of the required profiles needed. Test plans are developed that address, not only verifying the functional requirements, but also the standards compliance and interoperability testing needed to ensure a truly interoperable solution. The application interfaces, profile definitions, schemas, and test plans drive the design of the adapters necessary to implement the integration.
- Application adapter development
- ESB/middleware and Integration Configuration
IMPLEMENT With the proper design and documentation, the implementation of the application adapters can proceed in an organized manner. For messages, the IEC 61968-100 implementation profiles guide the configuration in the integration layer whether it is JMS, https, ESB or a combination thereof. For models, the IEC 61970-552 implementation profiles guide the integration of the model exchanges.
-
Functional, performance, and Interoperability testing
TEST Our IOP Approach to integration supports comprehensive testing of the solution to ensure compliance with requirements and fulfilling objectives while ensuring compliance with the standards and maximizing interoperability internally and externally.
- Training and hand-off
- Change management and maintenance
SUPPORT After the project is completed, we work to ensure complete understanding of the system for a smooth hand-off and long-term stability with system level training and long-term support and maintenance.
We work through the CIM-based integration process collaboratively with our clients and other third party vendors, to ensure that, as progress is made, staff knowledge is built and the overall approach for future integration projects is fully communicated. Our goal is to deliver our clients a repeatable and measurable process for implementing future integration projects independently.
PROJECT MANAGEMENT
We provide the following project and management support processes:
ASSURING INTEROPERABILITY
Our approach provides a full IOP methodology that maximizes industry accepted interoperability of the developed integration interfaces. The IOP Approach includes:
Step 1
Familiarity with all interoperability related documents from NIST, SGIP, UCAIug, CIMug, etc. to ensure all salient requirements are addressed in each project and review of additional interoperability related documents required for your project.
Step 2
Interface Compliance testing that will validate the message definition and the integration patterns used in the Integration Layer. This phase includes all message and integration specification definition.
Step 3
Use Case Interoperability testing that will fully test the interoperability of all the systems defined in the Use Case using the validated messages and integration patterns.
Step 4
And, if necessary, we will also prepare submission packages for the standards bodies to ensure lessons learned and appropriate standard extension proposals are submitted to the appropriate standards body.
ESTABLISHING A REFERENCE ARCHITECTURE
Architecture Goals and Principles
Integration contextual architecture
(patterns of information exchange, patterns of ownership)
Integration formal architecture
(adapter/component build and deployment practices, including development tooling)
Integration abstract functional architecture
(security and performance requirements for all enterprise information assets and integration components)
Enterprise Semantic Model
based on the CIM and client information assets.
Integration into the client’s cyber-security framework
GOVERNANCE DEVELOPMENT
Development of governance recommendations for enterprise information assets and application integration, impact on the client’s Software Development Life Cycle (SDLC) processes and desired evolution of the client’s internal skillsets. Specific deliverables include the development of Integration development and support lifecycle and integration with the client stage gate process (SDLC) including the steps below:
QUALITY ASSURANCE
Detailed and active cooperation in quality assurance activities, including design reviews, factory testing, system acceptance testing and security evaluation for all components. Our approach includes working with the client and third-party vendors to define and document any ongoing Quality Assurance processes and procedures that need to be implemented.